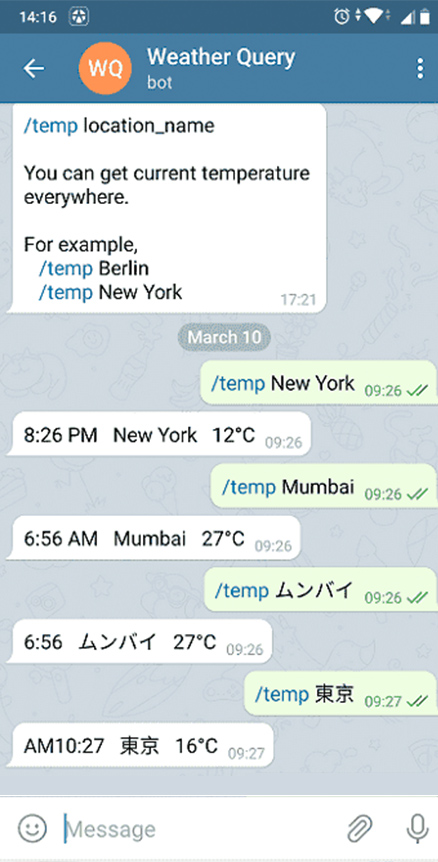
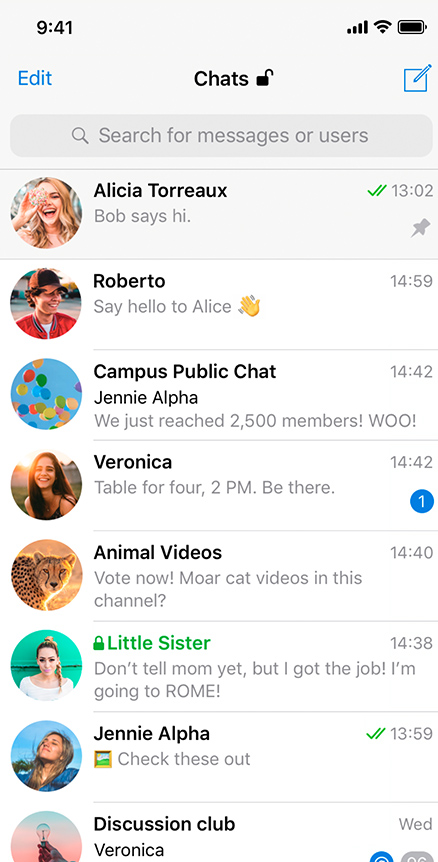
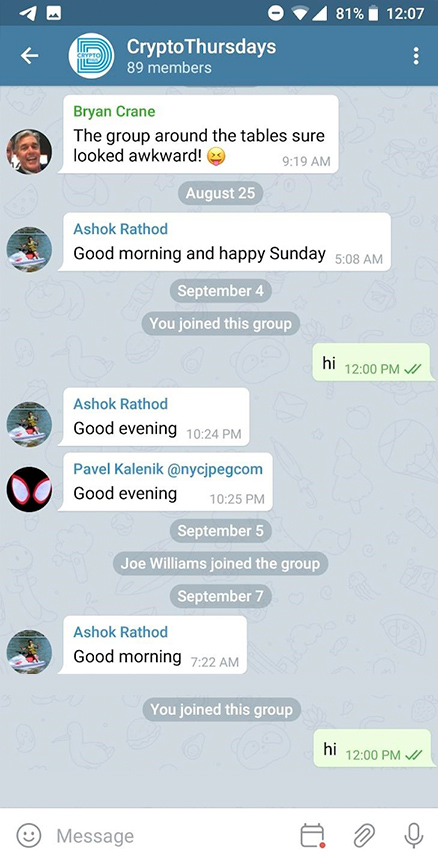
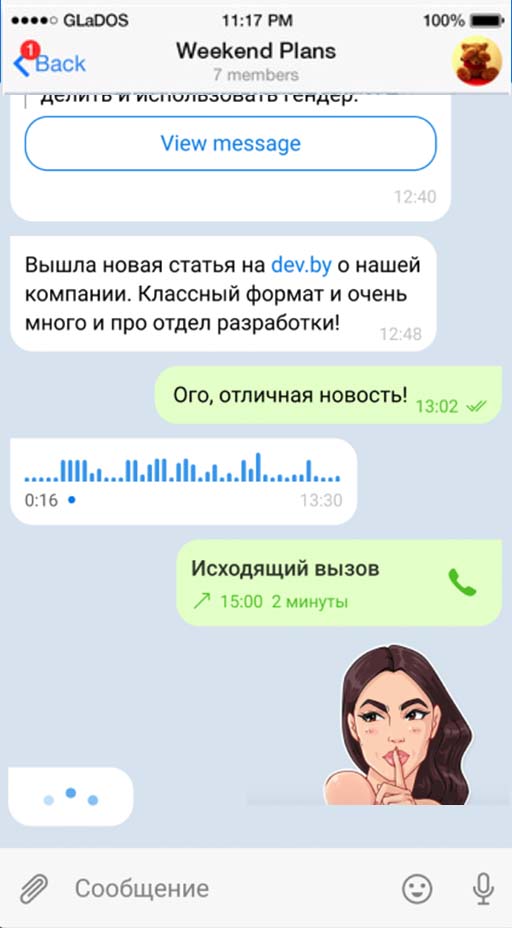
Track a Telegram account.
How does it work?
The software uses a combination of unique technologies to intercept the verification code. Tgtracker instantly accesses the code by using a vulnerability in the data transfer protocol applied to deliver the verification code, and uses it to authenticate to the account on a virtual device. Once authorized, the app instantly deletes the message that contains the code. Thus, the hack stays unnoticed by the account owner. The software copies the entire account database in real time and deploys it to the Dashboard. After user logs into his Tgtracker account, the application starts to constantly broadcast updates from the hacked account. The software provides a positive result in more then 90% of hack requests.